TRUSTED BY COMPANIES ACROSS EVERY INDUSTRY
Verisoul vs. Competitors












Fewer false positives (30–50%+)
IPQS relies on static IP blocklists, which frequently misclassify legitimate users. Verisoul analyzes live network traffic, catching only true proxy and VPN activity.
Result: Wiza reduced false positives by 90%; Adscend Media reported a drastic reduction.
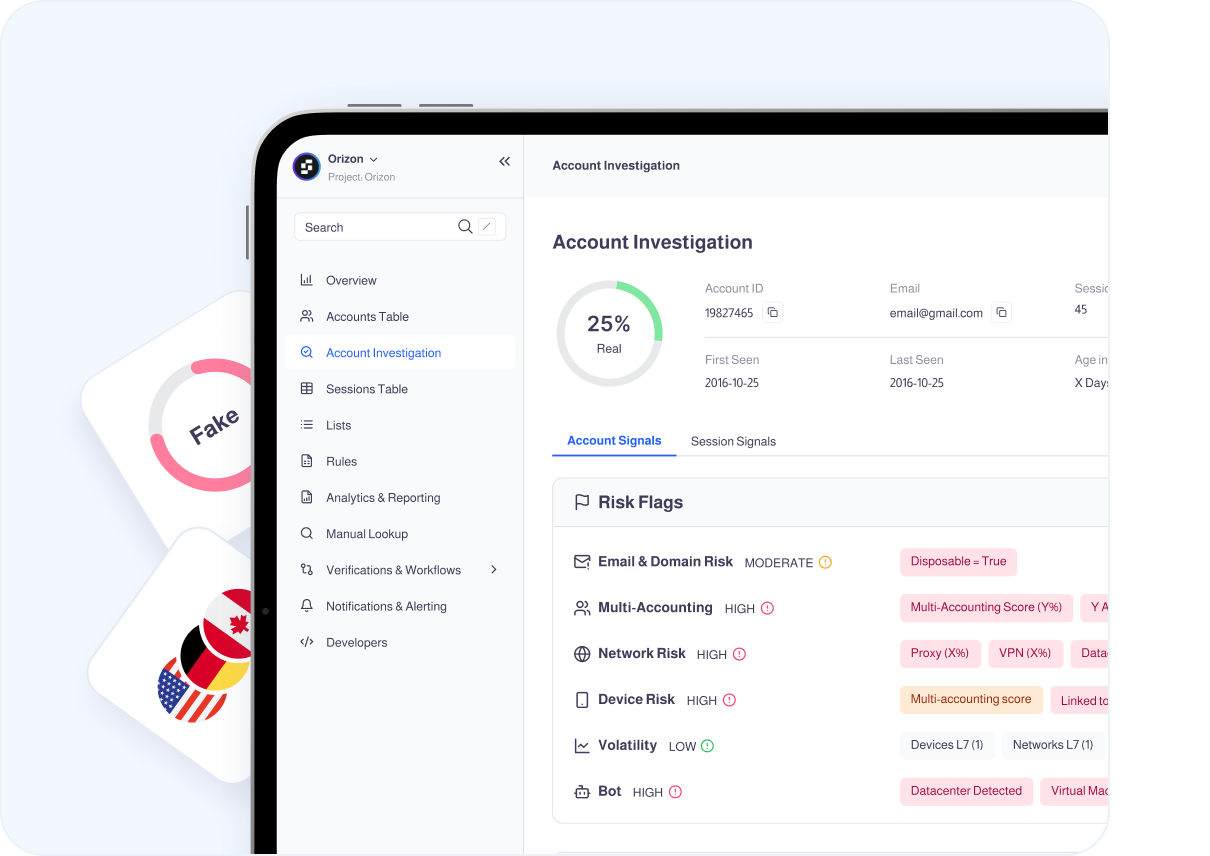
Holistic fraud decisions
Verisoul combines network, device, behavioral, email, and cluster-level intelligence into a single risk score, while IPQS surfaces fragmented signals.
Transparent scoring and rules
Customers describe IPQS as a “black box.” Verisoul provides clear, configurable fraud scores and rules teams can trust and tune.

Prevent fake accounts
Stop automated signups and low-trust accounts before they access voice, SMS, or messaging infrastructure. Verisoul evaluates email quality, identity signals, device behavior, and bot activity in real time to block abuse before it creates cost or risk.
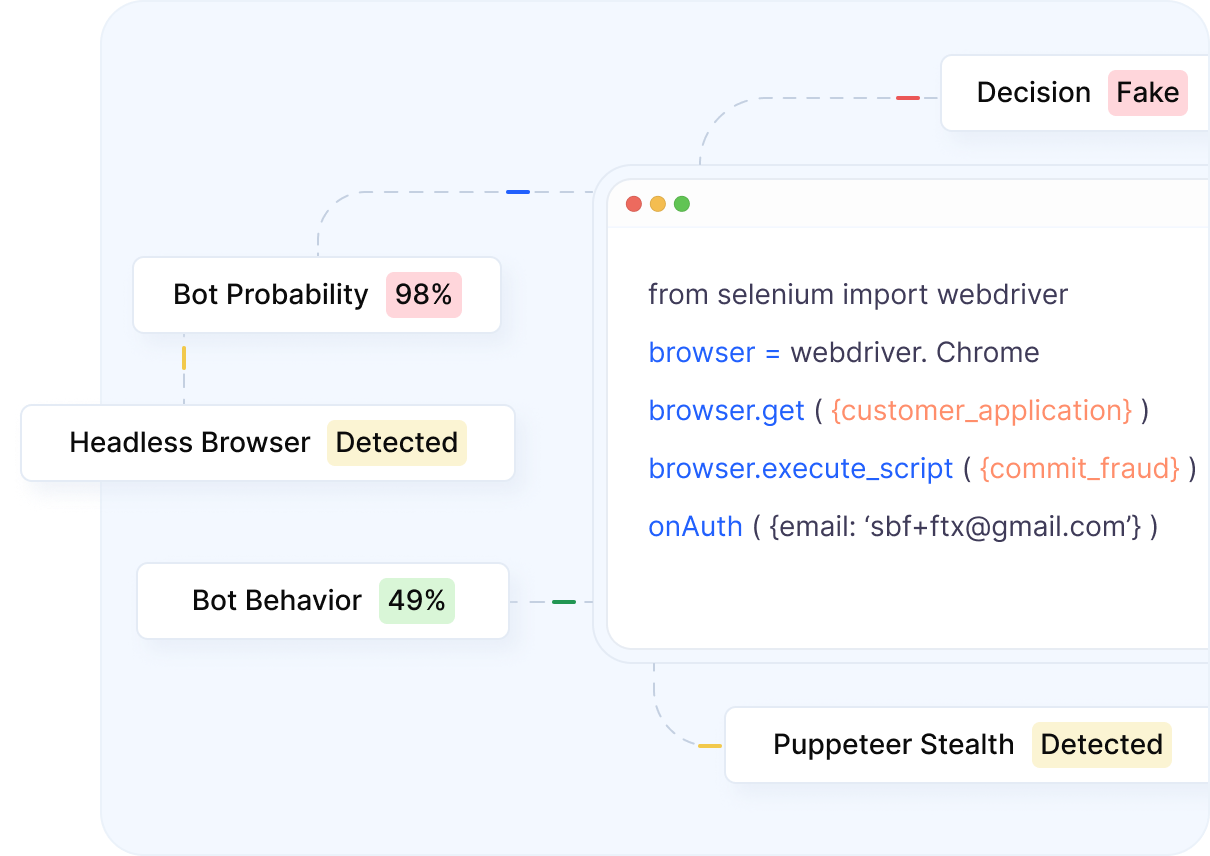
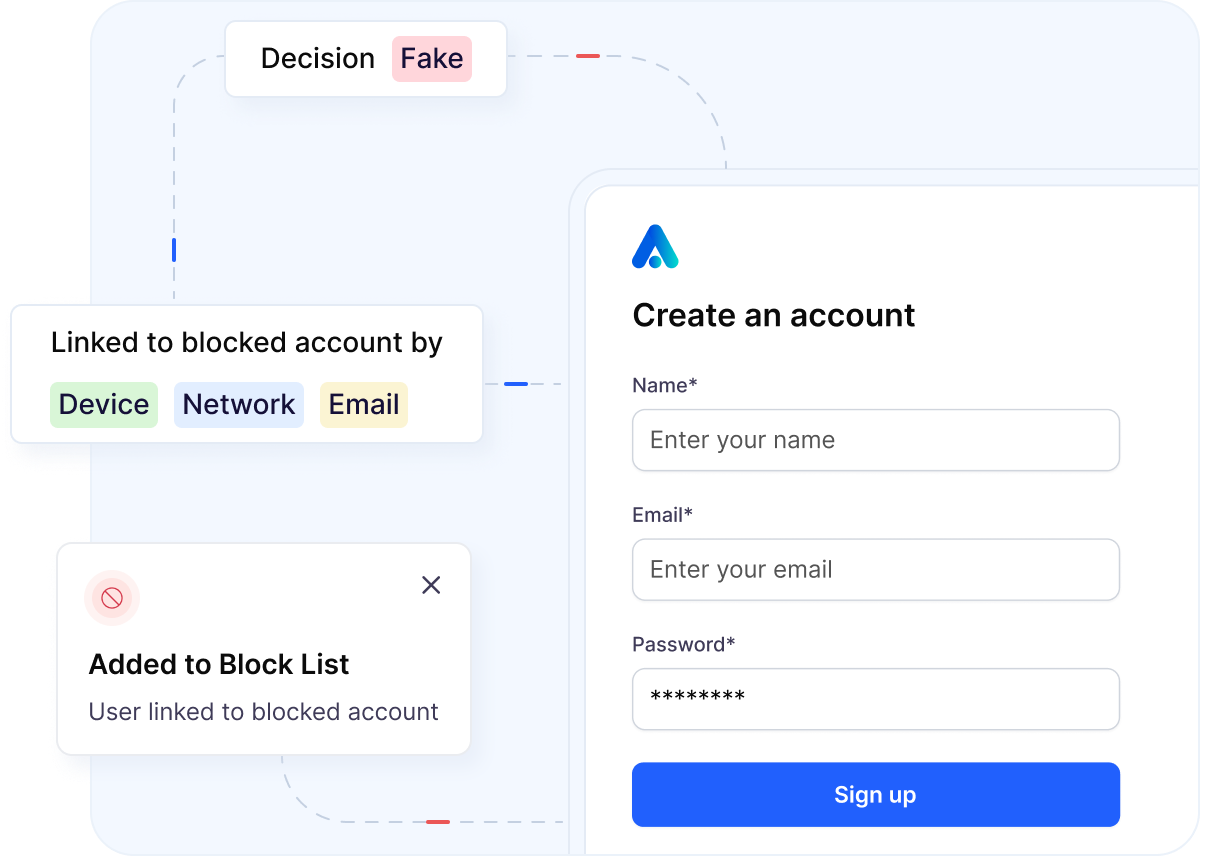
Block repeat spammers
Detect users you have already banned, even when they rotate emails, IPs, or devices. Verisoul links new accounts back to known spammers using identity, device, and network signals.
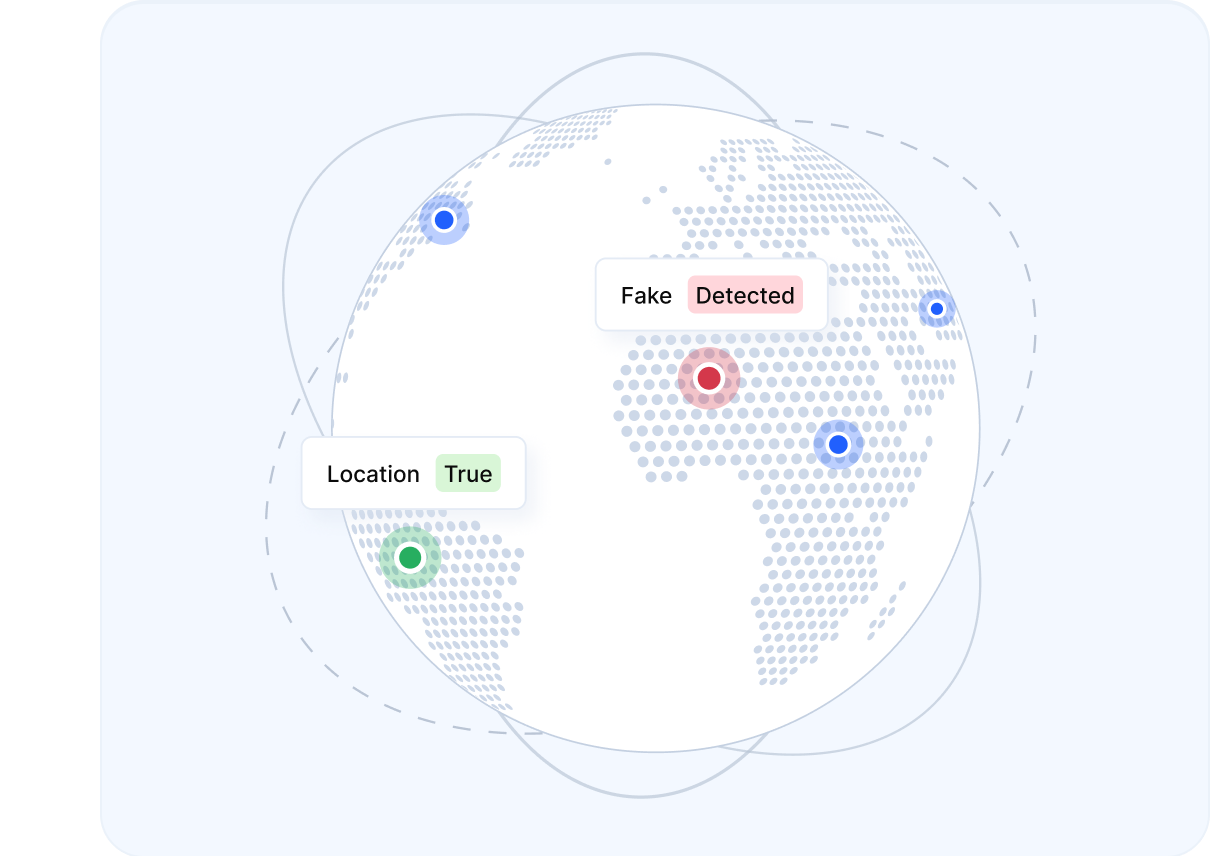
Detect proxies and location fraud
Identify mobile proxies, residential proxies, VPNs, and location spoofing used to bypass geographic and carrier controls. Verisoul uses active network forensics and device context to validate where traffic is truly coming from.
Stay compliant
Maintain a clear audit trail for every fraud decision. Verisoul provides deep signals, scoring, and rationale on each user so teams can explain, review, and defend enforcement actions.
Detect proxies and location fraud
Identify mobile proxies, residential proxies, VPNs, and location spoofing used to bypass geographic and carrier controls. Verisoul uses active network forensics and device context to validate where traffic is truly coming from.